APT, Advanced Malware, or Targeted Threat?
Please Note: This is the fourth article in a series. To start from the beginning, please click here.
It seems as if you can’t go a day without reading a blog or news headline mentioning the loss of sensitive corporate data due to hackers successfully carrying out advanced persistent threat (APT) attacks. Are APT attacks really that frequent and how concerned should you be about them? In order to answer these questions, we must understand what an APT attack looks like and how it differs from other attacks.
According to IE’s IT Security and Compliance Consultant, Jason Smith, an “actual APT is very rare due to the expense and complexity.” So why do we hear about data breaches referred to as an APT event so frequently?
APT DEFINED
Wikipedia defines an APT as “a set of stealthy and continuous computer hacking processes, often orchestrated by human(s) targeting a specific entity.” Based on this, it’s easy to understand why many would choose to use the term when talking about a data breach. That and “advanced persistent threat” just sounds more ominous and more demanding of attention and urgency than “targeted threat.” Smith points out that the vague understanding and misuse of APT as a term could be because the complexity of the process and actual cost required to launch an attacked aren’t widely known or discussed.
An APT attack involves communication to and from the infected machine that’s low and slow using command and control (C2) servers. “Meaning that it is almost certainly encrypted and emits small traffic bits of information over a long period of time,” Smith goes on to say. It also typically requires hundreds of thousands of dollars to launch a single attack. The cost is high because hackers have to design the APT chain it will deliver to the target network. They do this by either building it themselves, which is very time-consuming, or by purchasing it on the dark web.
APT ON THE RISE
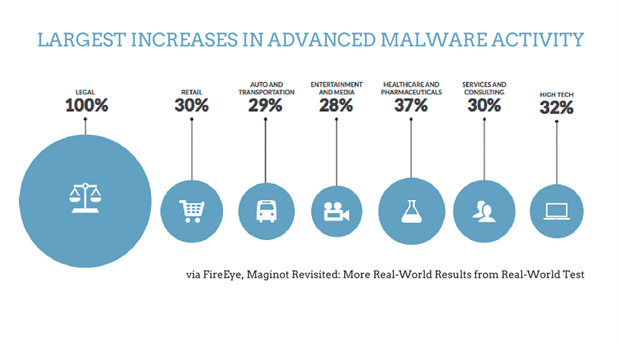
If actual APT attacks are costly, rare, and complicated, does this mean that they aren’t a concern? Absolutely not. As technology adoption advances and more data is stored and shared, the likelihood of these attacks moving beyond their usual defense contractor and military targets will also continue to rise. In fact, we are already starting to see this happen. In their report, Maginot Revisited, FireEye reported an average of 96% of the networks they studied had been breached and 27% of those attacks involved advanced malware. (They use the term “advanced malware” to describe “tools consistent with those used in APT attacks.”) The largest increases in advanced malware attacks were seen in the legal, retail, and auto/transportation industries. The top three industries for concentration of advanced malware breaches were agriculture (50%), auto/transportation (40%) and education (37%) compared to the federal government taking the number four spot (36%) and aerospace/defense down at number seven (30%).
A DIFFERENT KIND OF MALWARE
If it isn’t an APT attack, then what is it? Most likely it’s a targeted malware attack. The term isn’t as attention grabbing, but targeted attacks are no less serious in the damage they can inflict. The difference is they’re designed to get in and out very quickly to avoid detection rather than being stealth-like and hiding in plain sight like APTs.
What makes both so successful? Social engineering. Social engineering is used in 91% of APT attacks. It uses trusted and factual information to gain the trust of individuals within a target company, and the adoption of this tactic is what makes targeted attacks more successful than other blind attacks. For example, some targeted malware campaigns have sent emails, purporting to be from the target company’s IT department, asking users to click a link. That link directs them to a bogus website that either initiates an automatic download or gets the targeted individual to think it’s safe, and often necessary, to divulge sensitive information. This technique, tricking a user to click a link vs download an attachment, has seen a huge increase in use, from 7% to 41% in 2014.
Why has this approach been so successful? Social media and networking platforms like Glassdoor, LinkedIn, Facebook, etc. have increased the amount of information readily available, making it incredibly easy for threat actors to create target profiles on companies, as well as individuals. Now their easiest way into your network is through employees giving them access.
PREVENTION
It’s estimated that five malware events happen every second – that’s 432,000 per day. Since 90% of malware attacks capitalize on computer bugs left unpatched, some since 2002, an easy way to decrease a malware attack’s success rate is to patch your computers. However, your best bet of prevention is through security process, continuous monitoring, and the training and education of staff. According toFireEye, 69% of compromised victims are notified by external parties versus 31% of attacks being found internally. If a threat or suspicious activity is noticed, individuals should be trained to report the event immediately to decrease response time and impact. (You can learn more about how to turn your employees into security monitoring assets here.)
How can you detect suspicious activity? Some warning signs include:
· odd network behavior
· late night activity increase
· changes in the flow patterns of network data
WHAT’S NEXT?
Now that you have a better understanding of what differentiates APTs from targeted attacks and how they both use effective social engineering techniques, you can better educate your staff and develop a multilayered defense strategy. Of course you have to think beyond prevention. It’s absolutely essential to have an incident response plan, business continuity plan, and even cyber insurance in place for when the time comes that a hacker has been successful infiltrating your network and stealing your data. Having these assets can reduce your average cost per record lost or stolen, according to the Ponemon Institute.
Click here to view the next blog in the series. Want to start from the beginning? Click here.