Advances In Cybercrime Demand Greater Protection: A look at retrospective security versus point-in-time solutions
With cybercrime predicted to reach $6 trillion annually by 2021 and to be more profitable—and therefore, more attractive to criminal organizations—than the global combined trade of all major illegal drugs, businesses can no longer rely on traditional network security tools and expect to achieve protection.[1]
More than 75% of all current antivirus engines can’t detect advanced malware[2]
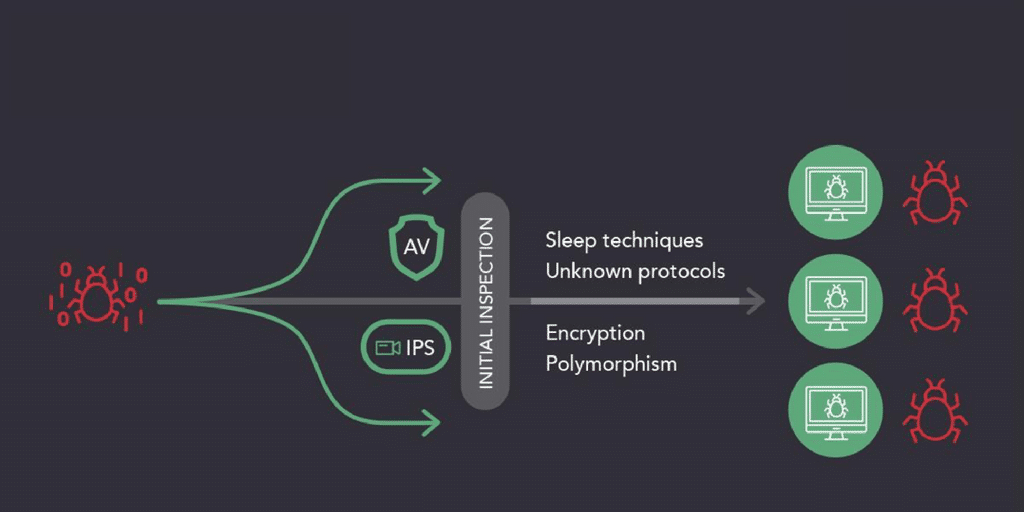
The hackers of yesterday knew only as much as they needed. Brute force was often their tactic of choice, requiring only minimal coding skills, an Internet connection and a criminal mindset. The Industry responded by developing Antivirus (AV) and Intrusion Prevention System (IPS) solutions that were adept at detecting and responding to these primitive though damaging cyberattacks. However, over time, hackers grew more sophisticated and began to employ new techniques to create advanced malware.
These unconventional hackers learned to exploit flaws in traditional AV and IPS solutions, tricking them into making inaccurate assumptions about the safety of file attachments. And, once inside the network, traditional tools did not continue to monitor the files to ensure that they are truly benign. That’s when the balance of power changed between hackers and the rest of the world.
Point-in-Time vs. Retrospective Security
Traditional security tools that employ Point-in-Time Security Systems examine files attached to email and text messages only once, at the point of entry. The tool uses a preconceived set of rules. If the attachment meets those conditions and appears to be safe, the email or text and its attachment are allowed into the network. This method of security eliminates the majority of potential threats, but fails to protect against advanced malware techniques, including polymorphic and environmentally aware viruses that can dupe point-in-time security tools into assuming the malware is safe.
Advanced malware protection solutions use Retrospective Security Tools. These solutions examine files and attachments not only at the point of entry, but also monitor them for as long as they are within the network. This approach allows IT to gain visibility into the entire attack continuum by continually logging information. This establishes a record of the file and its effect on the network before, during and after an attack, empowering IT to analyze the event and formulate a course of action.
Retrospective security protects against modern cyber threats
As hackers change their tactics by using encryption, sleep techniques as well as polymorphic and environmentally aware viruses, IT needs security tools that offer visibility into their systems at any past point in time. The retrospective security solution toolbox also includes attack chain correlation, behavioral indications of compromise (IOCs), trajectory and breach hunting in addition to retrospection. This enables IT to see exactly how their network has changed, providing the context that point-in-time security systems cannot deliver, while also showing the malware’s trajectory as it had spread through the network.
The increased visibility from retrospective security enables IT to:
- Methodically analyze what events transpired during a breach
- Learn how their system was entered and what data hackers had accessed
- Prevent similar future attacks
Retrospective security can also reduce remediation spending
In the event of a breach, an organization using a point-in-time security solution must engage a security consulting firm to perform forensics. However, if the company had instead used retrospective security tools, their IT managers would have access to all of the information necessary to investigate the breech and devise a strategy to tackle the security issue.
Defend against malware by increasing visibility into your network
While no network security tool can prevent 100 percent of malware from entering the network, an advanced malware protection solution using retrospective security tools can enable your organization to better secure itself against current and future advanced cyberattacks.
To learn more about how we’re working with Cisco to provide our customers enterprise-grade AMP retrospective security solutions, download:
 eBook: Prevent Cybercrime with Cisco Advanced Malware Protection (AMP) for Endpoints - Defend your organization with the power of retrospective security
eBook: Prevent Cybercrime with Cisco Advanced Malware Protection (AMP) for Endpoints - Defend your organization with the power of retrospective security
 Infographic: Real Security Calls for Advanced Malware Protection (AMP)
Infographic: Real Security Calls for Advanced Malware Protection (AMP)
Sources
[1] https://www.prnewswire.com/news-releases/cybercrime-damages-are-predicted-to-cost-the-world-6-trillion-annually-by-2021-300540158.html
[2] https://themerkle.com/emotet-banking-trojan-outsmarts-75-of-all-antivirus-software/