Maximizing Cisco Identity Service Engine (ISE) in Your Environment
Networking | Network Access Control | Cybersecurity | Identity Management
Have you heard this recently, “You need better network segmentation?"
Threat actors are bolder and more creative than ever before, which is why the growing need for sufficient network segmentation is not going away anytime soon. Think of network segmentation as a maze with your sensitive data guarded at the center. As your maze becomes more elaborate— i.e. You improve your network segmentation and security practices — the more difficult it will be for threat actors to navigate and eventually capture your prized data. This growing need for a more elaborate ‘maze’ is exactly why solutions like Cisco Identity Service Engine (ISE) or ‘ISE’ exist.
So, what is ISE exactly, and how can you maximize it for your environment?
Cisco Identity Services Engine (ISE) is a powerful tool that enables efficient and secure network access control and policy enforcement.
Commonly, we’ve seen businesses deploy Cisco ISE and leave it in monitor mode, to ensure that when it begins enforcing it won't break anything. This begs the question, why invest in a technology resource with robust capability, when you lack the staffing or intention to use it to its fullest potential?
We all have budget restraints, and buying pricier solutions is a losing game when you don't lean into your investment and reap the cost-saving benefits that come with proper utilization.
Below we’ll discuss how you can use Cisco ISE to its fullest potential within the specific requirements of your environment.
We are going to address:
- Initial Assessment and Planning
- Your Goals for Cisco ISE
- Cisco ISE Features & Capabilities to Consider
Lastly, we’ll provide some Cisco ISE implementation recommendations that can help optimize your success with this solution. Let’s get started.
Initial Assessment and Planning:
Before implementation, assess what your goals are and plan how Cisco ISE will fit into your existing infrastructure and security strategy. This includes identifying types of users, devices, and access requirements in your network.
It’s a lot to consider, so we’d recommend 4 steps to get you started.
Step 1) Begin Your Data Categorization - or how you’d like/need your data organized. Many times, this is defined by your compliance and ISE matches most of those, but they can be customized. This may take some time, but there are some tools, like Varonis, to make this easier.
Step 2) Determine Your Role-Based Access Control (RBAC) Setup – define the roles in your company and decide which data they will have access to. This process can be made easier by engaging with your HR team and aligning the RBAC to your user provisioning process. Many organizations choose to leverage an ITIL service catalog in these steps.
Step 3) Define your data flows – this includes data flow mapping or determining how data is processed, transformed, stored, and transmitted between different components or entities. If you process credit cards and must be PCI-DSS compliant, this step meets one of the requirements. Consider leveraging a tool like Varonis.
Step 4) Define your network segmentation goals based off of your data flow maps. - You can determine this by considering two factors:
- Data you’d like to segment for practical reasons
- Data you’d like to segment due to compliance requirements (ex: PCI, HIPAA, etc.).
Once you’ve determined the above, you’ll need to decide which mode/ modes of Cisco ISE will best help you manage and protect your data most effectively. That's a more technical discussion and we'll expand on ISE modes and their best use cases in a part 2. So make sure you subscribe to our blog to get notified when we release it!
Your Goals for Cisco ISE
At this point, you have an idea of where to start with implementation. You’ve reviewed your environment, identified how you want data to flow, etc. The next questions, before we review ISE features and capabilities are, “What do you want to accomplish with ISE?” And “What are your goals?”
Below are the two main goals that we most often see from people utilizing Cisco ISE.
Network Segmentation:
Many organizations strive to enforce access controls that prevent lateral movement of threats within your network. With Cisco ISE you can implement network segmentation based on user roles, device types, and security requirements as we’ve already discussed.
Continuous Monitoring and Optimization:
This goal revolves around maintenance of your security practices and network access controls. With Cisco ISE, you can regularly review your access policies, device profiles, and security posture assessments. This allows you to fine-tune policies and adjust configurations as your network evolves to ensure optimal performance and security.
These are two of the biggest overall benefits that Cisco ISE can bring to an organization, which is why you should avoid underutilization. Compliance regulations and new cyber threats will only challenge your network defenses, it pays to have goals and a strategy in place that evolves with demand.
Cisco ISE also provides a foundational understanding and some of the required technical capabilities for more advanced network technology such as Cisco Application Centric Infrastructure (ACI) and Cisco Digital Network Architecture (DNA).
Cisco ISE Features & Capabilities to Consider
Cisco ISE offers a robust feature set to ensure you have total visibility over your environment, you’re meeting compliance standards, and you’re protecting your network access.
Logging and Reporting:
Utilizing the logging and reporting features of Cisco ISE should be the minimum if you’ve invested in the technology. Configure logging and reporting to monitor network activity, track policy violations, and generate compliance reports. The information you acquire from these reports can help you identify trends, troubleshoot issues, and demonstrate compliance to auditors.
Authentication Methods:
Cisco ISE, like most network access control technologies, uses 802.1x. And to be clear, 802.1x is not a form of authentication, it is simply the authentication for ISE and other NAC. ISE can utilize a variety of authentication methods (supplicants), such as EAP (Extensible Authentication protocol), MAB (MAC Authentication Bypass), Active Directory, and guest access portals.
Most organizations get significant benefits by leveraging their Active Directory and existing group structure with their ISE deployment. Combine multiple methods to create a layered security approach or to meet their business requirements.
Network Access Control is an integral part of creating a zero-trust environment.
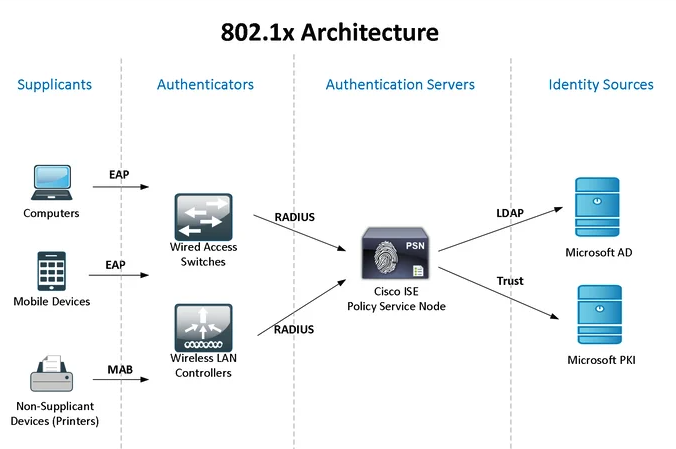
Image source: [2]
Guest Access Management:
Through this feature you can configure self-registration portals, sponsor-based access, and customizable guest workflows to manage guest access efficiently.
By implementing the guest access feature to provide secure Wi-Fi access to visitors, you can keep sensitive data safe and secluded from unintended access.
Threat-Centric NAC:
Integrate threat intelligence sources and security tools, and SIEM systems like Elasticsearch, Splunk, Microsoft Sentinel, and more. Leverage ISE's capabilities to detect and respond to threats by dynamically adjusting access policies based on real-time threat information.
External Identity Source Integration:
Integrate Cisco ISE with your organization's existing identity sources, such as Active Directory or LDAP, for seamless user authentication. This ensures consistent identity management across the network.
These are just a few of the features available to you through Cisco ISE. If you find yourself not leveraging any of the ones listed above, it might be time to re-evaluate your utilization and consider a security risk assessment. You’ve invested in the solution, make sure you use it!
Endpoint Compliance and Posture Assessment:
Leverage Cisco ISE's posture assessment capabilities to ensure that devices connecting to your network comply with security policies. Evaluate the health and security status of endpoints and enforce remediation actions if necessary.
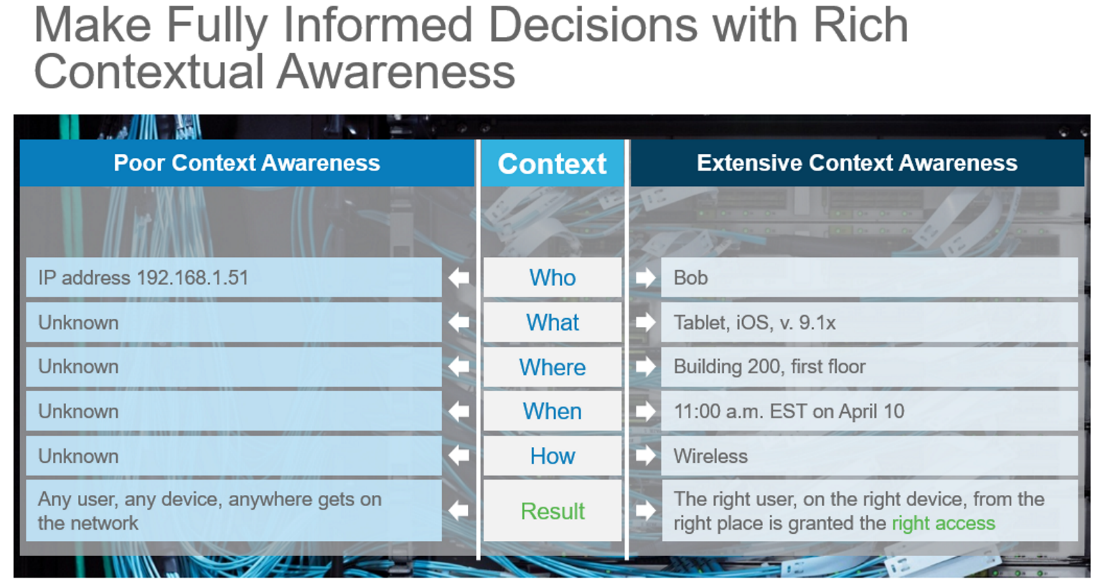
Contextual Profiling:
Cisco ISE integrates with multiple network devices, such as switches, routers, and wireless controllers. This integration enables ISE to enforce access policies at the network level and dynamically adjust access based on contextual information.
You can Utilize contextual profiling to gather detailed information about connected devices, including device type, operating system, and applications. This information enhances the accuracy of access decisions and helps in identifying unauthorized devices.
See how Cisco ISE can expand your contextual awareness below.
Cisco ISE Implementation Recommendations
Define Access Policies:
Create granular access policies that align with your organization's security and compliance policies. These policies determine who can access what resources and under what conditions. Leverage ISE's Policy Sets to manage different types of access scenarios. This comes down the road. 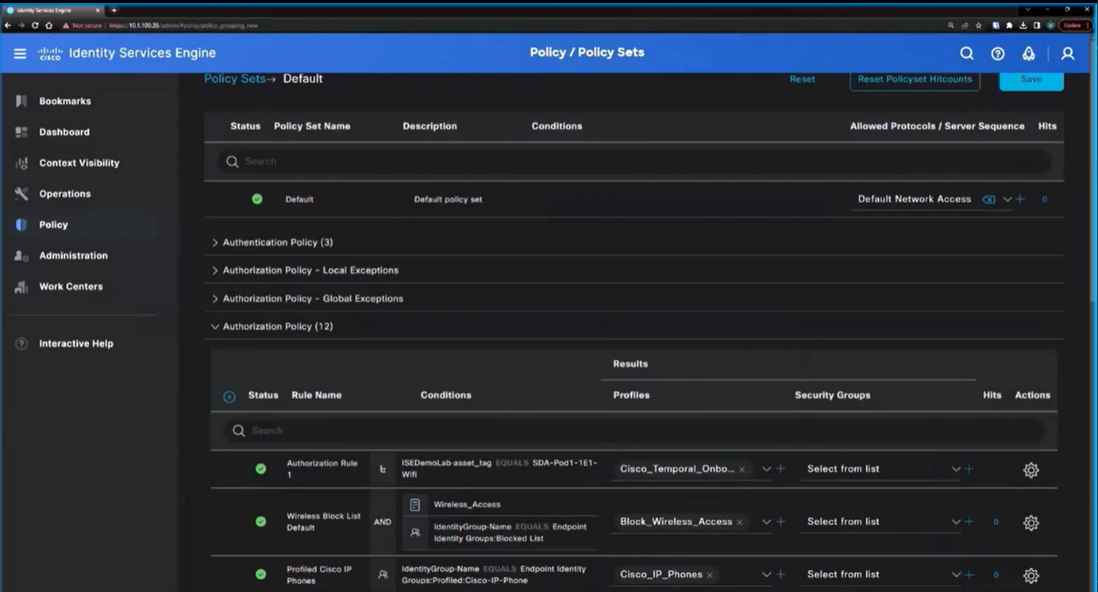
Training and Expertise:
As with any technology, full implementation requires an understanding of the solution. Consider utilizing an IT Consulting company or investing in Cisco ISE training for your employees. Also be sure to stay updated with Cisco’s new releases, features, and security updates through training, documentation, and community resources. Cisco ISE is a robust cybersecurity solution that, when implemented correctly and specifically for your environment, could save you money and reduce risk in the long term.
Collaborate with Cisco Communities:
If you plan on keeping Cisco ISE management in-house, consider engaging with Cisco's user communities, forums, and support resources to share experiences, ask questions, and learn from other professionals using it.
Tailor ISE’s features and capabilities to address your organization's specific needs and consider seeking guidance from Cisco experts to ensure you're leveraging its full potential. If you’re worried that you don’t have the staff to maintain Cisco ISE, consider bringing in an experienced Cisco ISE consultant!
How IE can help you fully implement Cisco ISE in your environment
If you need the coverage that ISE can offer but lack the staffing or specific expertise to run it properly, consider investing in an IT Consulting company who can take this solution and run it for you. At IE, our assessments and consulting will help you shorten deployment times, get more from your technology investments, and could save you money.
Our team can assist you in identifying which Cisco ISE features are essential for your organization and which ones you can do without. This will help ensure that you don't over-invest in unnecessary features and functionalities.
IE's Cybersecurity Experts can guide you through the intricacies of Cisco ISE
Our team of cybersecurity experts at IE are well-versed in the inner workings of Cisco ISE. We can assist you in determining which features, modes, and functions you should invest in for Cisco ISE.
Sources:
[1] https://www.cisco.com/c/en/us/support/docs/switches/catalyst-6500-series-switches/10570-41.html
[2] https://www.lookingpoint.com/blog/ise-series-802.1x